The Defense Advanced Research Projects Agency, DARPA, recently launched a new classified program to develop “transformative tools” to rapidly reverse-engineer and exploit vulnerabilities in emerging technologies and commercial cyber-physical systems.
DARPA has not formally announced the new program, and much of the project is expected to be shrouded in secrecy.
However, pre-solicitation documents obtained by The Debrief reveal the effort will be run out of the DARPA’s Microsystems Technology Office under the moniker: “Faithful Integrated Reverse-Engineering and Exploitation,” or “FIRE.”
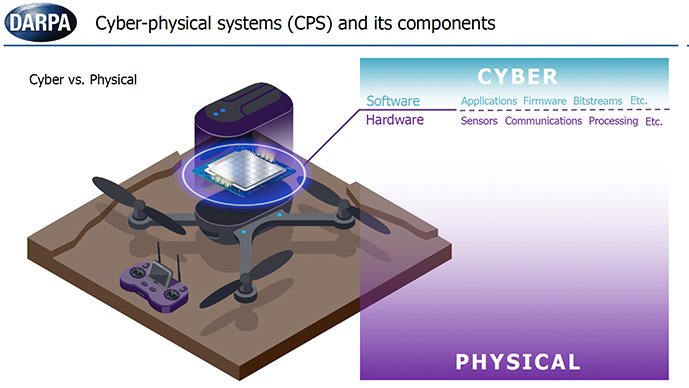

In a late March presentation to potential industry partners, DARPA officials explained that FIRE will focus on vulnerabilities in commonly used cyber-physical systems, such as energy grids, autonomous automobile systems, medical monitoring, or industrial control systems.
The primary goal of FIRE is to develop new ways to quickly “find, exploit, and patch vulnerabilities in medium-complexity cyber-physical systems.” DARPA notes that the tools developed in FIRE must achieve these goals at an unprecedented pace of at least a month of receiving hardware for analysis.
“The FIRE goals are driven by the proliferation of low-cost commercial-off-the-shelf (COTS) components (e.g., sensors, actuators, and algorithms) resulting in diverse classes of CPS including smart meters, medical devices, autonomous vehicles, and industrial control systems to name a few,” reads a broad agency announcement issued by DARPA on March 15.
“Furthermore, agile development practices have shown that even highly complex systems such as cars can be remotely patched every few weeks. Innovative CPS vulnerability analysis tools and techniques are needed to keep pace with increased system diversity and decreased analysis timelines.”
Documents clarify that DARPA is not interested in tools that independently address cyber or physical vulnerabilities. Instead, FIRE is focused on how the composition of hardware, software, and physical components can make technology systems uniquely susceptible to attack.
During the March presentation, DARPA offered a demonstration of the types of cyber-physical system vulnerabilities it’s interested in by showcasing an example of “how to crash a quadcopter using acoustics.”
Program officials explained how specific sound frequencies can inject false readings into the micro-electro-mechanical Systems (MEMS) gyroscope of a quadcopter, ultimately destabilizing the drone and causing it to crash.
The scenario used by DARPA is not hypothetical. Research by the Korea Advanced Institute of Science and Technology has demonstrated that a quadcopter drone can be downed by projecting sound frequencies under 30 kHz through a consumer-grade speaker.
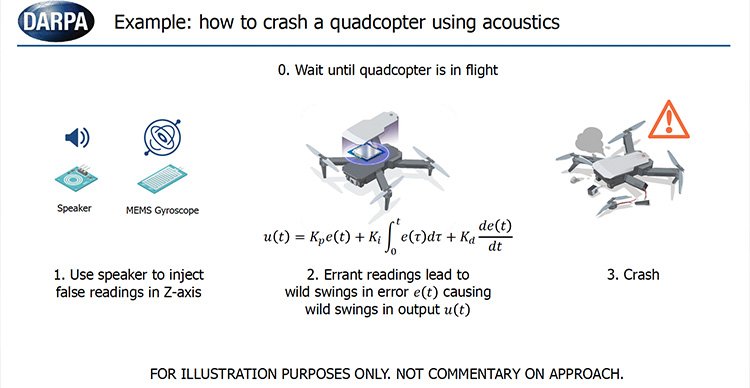

With this example, DARPA expects new analysis tools developed in the FIRE program to be able to identify that a quadcopter’s gyroscope is vulnerable to an acoustic attack; develop ways to exploit that vulnerability (e.g., using speakers to project sound frequencies toward a drone); and ultimately methods for nullifying a quadcopter’s vulnerability to acoustic attacks.
By taking this holistic approach, FIRE could provide the Department of Defense (DoD) with a new ways to identify and launch disruptive, asymmetric attacks on enemy systems in various sectors, including civil infrastructure, energy, healthcare, transportation, or manufacturing. Simultaneously, this same process can be used to better shore-up U.S. cyber-physical systems from similar threats.
DARPA notes the first step in the analysis process should involve reverse engineering a cyber-physical system by creating an identical “digital twin.”
With everyday items increasingly integrated with new and emerging technologies, the threat of cyber-physical attacks has become a significant concern.
Past research has demonstrated it is relatively easy to gain long-distance control, location tracking, or in-cabin audio exfiltration by exploiting vulnerabilities in the electronic control systems found in most modern cars.
“Once you have access to a vehicle, you pretty much have access to any part,” said Dr. Skanda Vivek, a physicist at Georgia Gwinnett College specializing in autonomous vehicle control. “If you get to one control unit – like the entertainment system, for example – then with some reverse engineering, you could control the steering wheel.”
“Industrial control systems,” or technologies enabling control, automation, and monitoring in industrial environments like electric plants, manufacturing facilities, and refineries, are mentioned as a key focus area for the FIRE program.
A large portion of DARPA’S FIRE presentation was also dedicated to identifying vulnerabilities to “maritime industrial controls systems” (ICS).
DARPA notes that many modern maritime ICS used for everything from powering a ship to processing wastewater “are becoming more intelligent and packed with ‘convenient’ features” that could be potentially exploited by malicious attacks.
Most of the FIRE program is expected to be cloaked in secrecy, and private companies or academic institutions working on the program are required to maintain active security clearances and facilities approved to store classified materials.
DARPA anticipates selecting industry partners and issuing contract awards for the FIRE program to occur by the fall of 2023.
If all goes according to plan, the first set of analysis tools for cyber-physical systems should be delivered by the spring of 2024, with the entire research and development process slated to run through mid-2027.
Tim McMillan is a retired law enforcement executive, investigative reporter and co-founder of The Debrief. His writing typically focuses on defense, national security, the Intelligence Community and topics related to psychology. You can follow Tim on Twitter: @LtTimMcMillan. Tim can be reached by email: tim@thedebrief.org or through encrypted email: LtTimMcMillan@protonmail.com

