Russia’s intelligence services are using custom malware to target Android devices to tap into Starlink satellite data, a recent Security Service of Ukraine (SBU) report warns.
The alarming development marks the latest chapter in a series of growing anxieties surrounding Starlink’s dominance of the global satellite internet landscape.
In a technical report obtained by The Debrief, Ukraine’s chief counterintelligence agency accused Russia’s military intelligence agency (GRU) of conducting “large-scale cyber attacks to obtain unauthorized access to Android devices possessed by Ukrainian military personnel for planning and performing combat missions.”
At least ten different types of malicious software were reportedly uncovered by SBU, including one that’s “functional purpose is to gather data from the Starlink satellite system.”


Starlink is the satellite internet constellation operated by SpaceX, the aerospace company founded by Elon Musk. With over 4,000 small satellites in low Earth orbit, Starlink provides high-speed, low-latency internet access to millions living in underserved and remote areas globally.
Starlink has also played a significant role in Ukraine’s communications network following Russia’s invasion in late February 2022. Thousands of satellite terminals are being used to replace internet services destroyed by the war.
Speaking with the New York Times, Ukraine’s Minister of Digital Transformation, Mykhailo Fedorov, underscored Starlink’s significance for civil and military use, saying, “Starlink is indeed the blood of our entire communications infrastructure now.”
Nevertheless, the dependence on Starlink and the company’s near total control of the global satellite internet market has become an increasing concern for officials, both in Kyiv and across the globe.
In February, SpaceX’s chief operating officer, Gwynne Shotwell, revealed that specific steps had been taken to prevent Ukraine from using Starlink for military “offensive purposes.”
“We were really pleased to be able to provide Ukraine connectivity and help them in their fight for freedom. It was never intended to be weaponized,” said Shotwell while speaking at a conference in Washington, D.C. “Ukrainians have leveraged it in ways that were unintentional and not part of any agreement.”
Mykhailo Podolyak, a senior adviser to Ukraine’s president, Volodymr Zelenskiy, responded by accusing Shotwell and Musk of failing to recognize Ukraine’s right to self-defense. In a message posted on X (formerly Twitter), Podolyak said companies needed to decide if they were on the side of Ukraine and “the right to freedom” or on the Russian Federation’s side and its “‘right’ to kill and seize territories.”
Citing unnamed sources “familiar with the situation,” The New York Times reported that Starlink communications have been restricted “multiple times” during the war, preventing Ukraine’s military from carrying out strategically significant operations, including the use of drones.
It is unclear, however, how many of the Starlink service disruptions have resulted from the SpaceX restrictions or jamming by Russian electronic warfare systems.
Another concern on the dependence of Starlink stems from SpaceX’s CEO and co-founder, Musk. At times, the outspoken and controversial Musk has been accused of being too pro-Kremlin or pro-Putin.
Last fall, Musk floated a peace proposal in a poll on X that included Crimea being formally recognized as part of Russia, new elections overseen by the U.N. for annexing territories currently occupied by Russia, and a Ukrainian promise of neutrality. “This is highly likely to be the outcome in the end – just a question of how many die before then,” Musk added.
Musk’s hypothetical bid to end the war drew the ire of Ukraine and its Western allies, as many saw it as tantamount to a Ukrainian surrender. “F— off is my very diplomatic reply to you,” Andrij Melnyk, Ukraine’s outgoing ambassador to Germany, wrote in response.
After receiving nearly 2.8 million votes, the final results of Musk’s poll showed 59.1% to 40.1% rejecting the peace proposal as a viable option.
Fiona Hill, one of the foremost American experts on Russia affairs, said it was “very clear” that Musk was “transmitting a message” for Russian president Vladimir Putin.
“Putin does this frequently. He uses prominent people as intermediaries to feel out the general political environment, to basically test how people are going to react to ideas,” Hill, a former member of President Donald Trump’s National Security Council, told Politico.
“This is a classic Putin play. It’s just fascinating, of course, that it’s Elon Musk in this instance because, obviously, Elon Musk has a huge Twitter following. He’s got a longstanding reputation in Russia through Tesla, the SpaceX space programs, and also through Starlink. He’s one of the most popular men in opinion polls in Russia.”
Ian Bremmer, head of the Eurasia Group, said that Musk told him he had spoken directly with Putin just before publishing his peace plan. The SpaceX CEO categorically denied Bremmer’s claim, saying he had only spoken with Putin “about 18 months ago” and that “the subject matter was space.”
The New York Times reported that diplomats from at least nine countries, “including in Europe and the Middle East,” had raised concerns with American officials about Starlink’s hegemony over the strategically significant field of satellite internet.
Speaking on a condition of anonymity, as they were not authorized to speak on the record, a senior official from the U.S. Intelligence Community told The Debrief that unease with Starlink had been discussed by the intelligence services of virtually every major U.S. ally.
“The lack of regulation, oversight, and being dependent on the whims of Elon is an issue for many people,” the official said.
The threat of hackers using malware to remotely hack Starlink data raises another concern with the service’s dominance over satellite communication.
Last year, Lennert Wouters, a security researcher at the Belgian university K.U. Leuven revealed hackers could run custom code to gain access to Starlink satellites by exploiting hardware vulnerabilities on the ground-based terminals.
At the Blackhat Security Conference in Las Vegas, Wouters demonstrated that a custom modchip using off-the-shelf parts costing around $25, could launch a “fault injection attack,” bypassing Starlink’s security protections and gaining access to its systems.
Starlink announced it had released a public update following the revelation. However, Wouters said the underlying vulnerability could only be fixed by the company creating new versions of the main chips in its satellite terminals.
Starlink currently operates a “Bug Bounty” program, offering rewards between $100 to $25,000 to security researchers that discover vulnerabilities in its satellite systems.
Among the trove of classified documents allegedly leaked on Discord by U.S. Air National Guardsman Jack Teixeira was an intelligence report revealing that Russia had been testing a secret electronic warfare system called “14Ts227 Tobol,” designed to disrupt Starlink communications.
It has been speculated that Tobal or Russia’s truck-mounted Tirada-2 satellite jammer may be responsible for reports of Starlink outages by Ukrainian forces during the grueling Battle of Bakhmut.
In a July report, Ukraine’s Computer Emergency Response Team (CERT-UA) warned that Starlink was placing Ukrainian soldiers at “increased risk.”
In the report, Ukrainian soldiers were urged to “immediately contact” the ITS Cyber Security Center if their electronic devices did not have installed Endpoint Detection and Response (EDR) class protection software.
“Computers located outside the protection perimeter, in particular those that use Starlink terminals to access the Internet, are at increased risk,” CERT-UA wrote.
This latest warning by SBU differs from the previous concerns over the hacking of Starlink systems. Rather than gathering information directly or disrupting Starlink systems, the malicious software dubbed “Malware 4. STL” reportedly uses a person’s mobile device to remotely collect data on Starlink systems.
“The malware collects all the data about the system that is available via API functions,” SBU writes. “[The] malicious files were used to download information about the configuration of connected Starlink satellite terminals.”
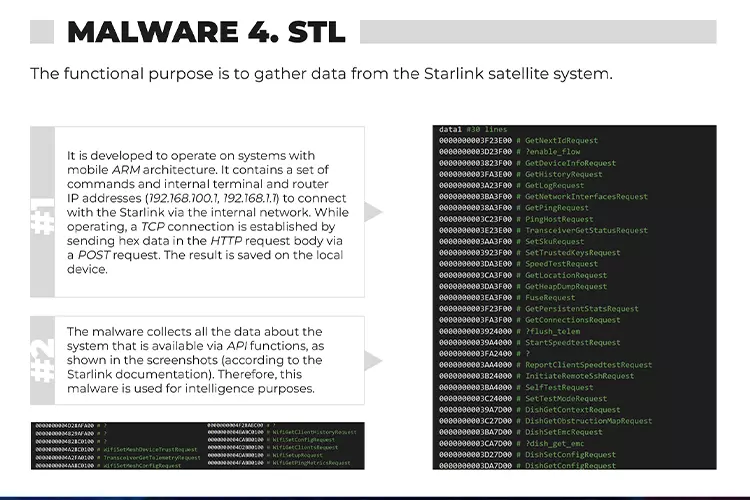

The SBU goes on to say that cyber experts had concluded Russia had attempted to spread the malware using “captured Ukrainian tablets on the battlefield.”
CERT-UA’s July report, the Ukrainian cyber-security agency said the recent malware attacks on Starlink networks were being carried out by former ‘officers’ of the State Security Service of Crimea, who in 2014 betrayed their military oath and began to serve the FSB of Russia.”
In the recent report, Ukraine’s counterintelligence agency reported that “SBU is highly confident that this activity originated from Russian military intelligence, particularly the hacker group Sandworm (military unit 74455).
Sandworm is a cyberwarfare and Advanced Persistent Threat unit, reportedly operated by the Main Directorate of the General Staff of the Armed Forces of the Russian Federation or GRU. The group has also gone by Telebots, Voodoo Bear, and Iron Viking.
The cyber warfare unit is believed to be responsible for numerous cyberattacks on Ukraine, in addition to interference efforts in the 2017 French presidential election and the 2018 Winter Olympics.
In 2020, the U.S. Attorney’s Office indicted six Russian GRU officers of being part of Sandworm and responsible for a host of cybercrimes. Scott W. Brady, U.S. Attorney for the Western District of Pennsylvania, described Sandworm’s activities as “representing the most destructive and costly cyber-attacks in history.”
Ultimately, as the digital age evolves, so does the nature of warfare, with nations using technology not just as tools but as the frontline of confrontation.
These recent revelations by the SBU concerning Starlink and the potential vulnerabilities in its systems underline the strategic importance of satellite internet in modern geopolitical conflicts.
With SpaceX’s near monopoly over the global satellite internet market and Musk’s often controversial stance in global affairs, the pressure may be mounting for an international consensus on the regulation and oversight of these vital systems.
Regardless, one thing remains clear: In the era of interconnectedness, the fight to protect, control, and exploit the digital realm is not just imminent—it’s already here.
Tim McMillan is a retired law enforcement executive, investigative reporter and co-founder of The Debrief. His writing typically focuses on defense, national security, the Intelligence Community and topics related to psychology. You can follow Tim on Twitter: @LtTimMcMillan. Tim can be reached by email: tim@thedebrief.org or through encrypted email: LtTimMcMillan@protonmail.com

