A group of Ukrainian hacktivists claim to have successfully hacked the email of Sergey Alexandrovich Morgachev, a Lieutenant Colonel with Russia’s military intelligence service, GRU, and alleged former head of the infamous Russian cyber-espionage unit known as “Fancy Bear” or “APT28.”
First reported by the open-source intelligence website Info Nampalm, the hack was supposedly carried out by the Ukrainian-based hacktivist group Cyber Resistance sometime in March.
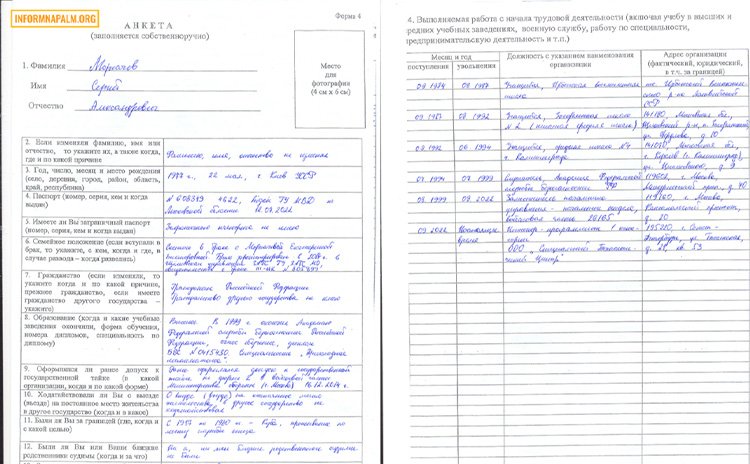
By infiltrating his personal email through undisclosed means, hacktivists say they uncovered a wealth of personal and professional information on Morgachev.
Some items seized included copies of Morgachev’s driver’s license, vehicle registration, residential lease agreements, family photos, and scanned copies of security clearance renewal applications.
Additionally, hacktivists say they accessed the GRU officer’s AliExpress account, where they carried out “a symbolic act of moral humiliation.” by ordering numerous sex toys and gay pride flags in Morgachev’s name.
The Debrief was able to examine some of the documents seized in the email hack but cannot independently confirm their authenticity. However, speaking on the condition of anonymity as they were not authorized to speak on the record, an official with the U.S. Department of Justice told The Debrief that some of Morgachev’s personal information disclosed in the emails appeared to be valid.


Morgachev is currently wanted by the FBI following a federal grand jury indictment of him and 11 other Russian intelligence officers for crimes related to their alleged roles in interfering with the 2016 U.S. elections.
A federal indictment filed by the Department of Justice states that Morgachev and his GRU cohorts “knowingly and intentionally conspired…to gain unauthorized access into the computers of U.S. persons and entities involved in the 2016 U.S. presidential election.”
The charges stem from activities attributed to one of Russia’s most notorious advanced persistent threat (APT) units, commonly known as “Fancy Bear.”
In addition to interfering with the 2016 U.S. elections, Fancy Bear is believed to have been involved in numerous cybercrimes spanning almost a decade.
The group has been suspected or accused of committing attacks against the networks of nearly every Western government and NATO; major corporations like Lockheed Martin and Raytheon; Western journalists; the World Anti-Doping Agency; the Dutch Safety Board investigating the shooting down of Malaysia Airlines Flight 17, among others.
In the recent email hack, hacktivists say they found scans of a recent security clearance renewal application showing Morgachev as the “Deputy Head of Directorate-Head of Department in military unit #26165” from August 2019-August 2022.

The 2018 indictment by the U.S. Special Counsel and Western intelligence reports have identified GRU Unit 26165 as being Fancy Bear.
On the clearance application, Morgachev lists his current job role as “Category 1 Programming Engineer” at the Special Technical Center LLC, at 21 Gzhatskaya Street, Apt. 53, in St. Petersburg, Russia.
According to the National Agency on Corruption Prevention of Ukraine, the Special Technical Center LLC is a defense company that provides equipment to the Russian military. The nonprofit organization which tracks entities providing support to Russia’s war against Ukraine lists the Special Technical Center as being sanctioned by the European Union, the United States, the United Kingdom, Canada, Switzerland, Japan, and Ukraine.
A resume in the email dump notes Morgachev as still working for the Russian Ministry of Defense. His listed duties include “managing special software development… including the personnel selection and control of department work, distribution of tasks, [and] interaction with other units.”
An income statement in his email shows Morgachev’s annual salary at the end of 2022 as nearly 3.6 million Rubles or $44,000.
Hacktivists say they also gained access to Morgachev’s anonymous social media accounts, where they posted scans of his passport and ID.
As for the AliExpress orders, Hacktivists shared screenshots of an online shopping cart filled with various items, including memorabilia with the FBI logo, a rainbow gay pride flag, two large black dildos, a leather ball gag, and a leather strap-on chin-mounted dildo.
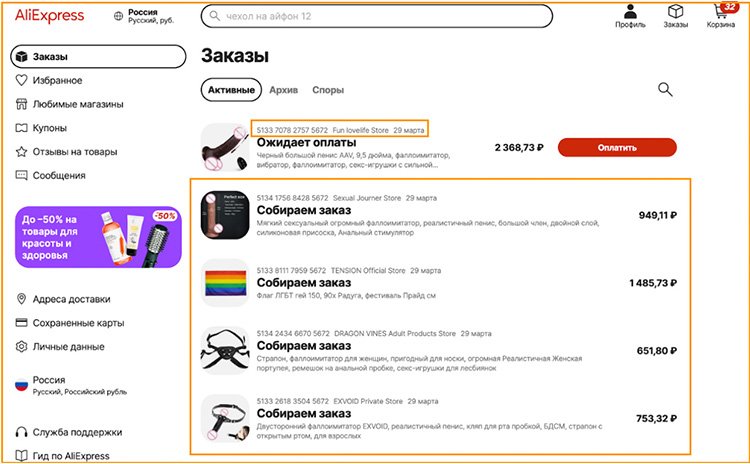

The items were reportedly paid for using Morgachev’s credit card information on file with AliExpress and delivered to his post office box in Korolev City, on the northern outskirts of Moscow.
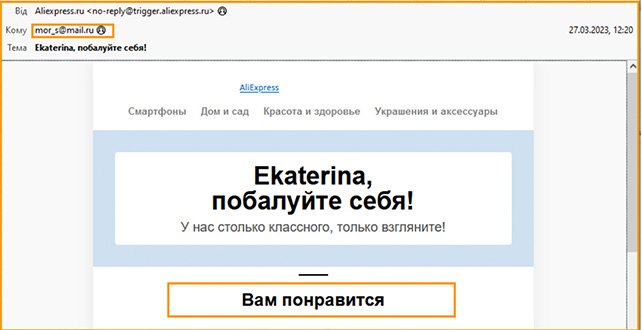
Hacktivists also shared a screenshot of an email from AliExpress dated March 27, thanking Morgachev for his recent order and notifying him his items were “already on its way.”

Cyber Resistance says they intend to make the complete dump of Margachev’s email files available so that “all interested parties, from the FBI to journalists, experts and members of the public, could independently investigate the facts set forth in this publication, and find other information that may be useful for further investigations.”
Info Napalm reported that links to hacked files, including English translations of the files, will be made available in the “near future.”
The Debrief reached out to the FBI for comment. However, the agency did not respond by the time of publication.
Tim McMillan is a retired law enforcement executive, investigative reporter and co-founder of The Debrief. His writing typically focuses on defense, national security, the Intelligence Community and topics related to psychology. You can follow Tim on Twitter: @LtTimMcMillan. Tim can be reached by email: tim@thedebrief.org or through encrypted email: LtTimMcMillan@protonmail.com

