Former president Donald Trump has recently found himself embroiled in yet another controversy, following an FBI search of his Mar-a-Lago resort and the recovery of classified documents being kept there. The Department of Justice (DOJ) alleges the former president unlawfully retained these and possibly tried to conceal them. Reportedly, Trump removed over 300 classified documents when he departed the White House in 2021.
Many of these classified materials were returned to the National Archives in early January. However, following the search of Trump’s Florida golf resort on August 8, the DOJ says FBI agents uncovered boxes full of classified government documents, including some retained at the highest classification levels.
The specific nature of the classified material allegedly taken by Trump remains shrouded in secrecy. The DOJ’s ongoing criminal investigation, however, has garnered unprecedented attention, casting a floodlight on an area of government that typically remains well in the shadows.
To cut through some of the confusion surrounding this intentionally hazy subject, The Debrief now takes a deep dive into the murky world of official secrecy to look at how the U.S. government tries to keep the lid on highly-sensitive, classified information.


What Is Classified Information?
The American belief in the importance of maintaining secrecy actually predates the United States, when on September 6, 1774, members of the first Continental Congress passed a resolution stating, “Resolved, that the doors be kept shut during the time of business and that the members consider themselves under the strongest obligations of honor, to keep the proceedings secret until the majority shall direct them to be made public.”
More than a century-and-a-half later, on March 22, 1940, President Franklin D. Roosevelt formed the modern process for handling national secrets by signing Executive Order 8381 and establishing the first-ever executive security classification directive.
In the ensuing 82 years, eight U.S. Presidents have reissued executive orders, modifying and updating what constitutes classified information and how it should be handled.
Currently, the U.S. classification system functions off Executive Order 13526, issued by President Barack Obama in 2009.
Under this directive, sensitive information can be designated into one of three levels of classification based on the damage to national security that could be expected if such information were improperly disclosed.
Those three levels and the expected damage from improper disclosure from lowest to highest are:
- Confidential: “Damage to national security.”
- Secret: “Serious damage to national security.”
- Top Secret: “Exceptionally grave damage to national security.”
Information that doesn’t fall into one of these three categories is considered inherently “Unclassified.” However, just because something is unclassified doesn’t mean it is still publicly accessible.
In 2010, President Obama also signed Executive Order 13556, establishing the “Controlled Unclassified Information” (CUI) program, covering information that is unclassified but still exempt from mandatory release to the public under the Freedom of Information Act (FOIA).
The CUI directive expanded on a similar memo first issued by President George W. Bush, attempting to establish uniformity for how the government handles unclassified but non-public information. By this time, various branches had been using over 100 different internal document designations for unclassified but FOIA-exempt documents.
To date, the CUI program has never been fully implemented, with agencies still using various procedural designations such as “For Official Use Only” (FOUO) within the DoD or “Law Enforcement Sensitive” (LES) by the DoJ.
In fairness, federal agencies displaying contempt for following classification rules is nothing new. Since the establishment of the classification system, Congressional oversight committees and government watchdogs have consistently uncovered federal agencies using countless unauthorized security controls to limit access to information.
The vast majority of classified information is now governed by presidential executive order. However, secrets involving nuclear weapons and nuclear energy are a horse of a different color.
Classified Nuclear Secrets: A Whole Other Ball Game
On July 20, 1946, Congress passed the Atomic Energy Act (AEA), outlining how the United States would control and manage nuclear technology.
Most significantly, the Bill ruled that the development and management of nuclear power would fall under civilian control, taking nuclear weapons out of the hands of the military and under the authority of the newly established Atomic Energy Commission (AEC).
The 1946 AEA also established that “all data concerning the manufacture or utilization of atomic weapons, the production of fissionable material, or the use of fissionable material in the production of power” would be designated as “Restricted Data.”
By legislation, Restricted Data was to be outside the scope of the three then-existing classification levels established by President Roosevelt’s E.O. 8381: Secret, Confidential, and Restricted (the term and corresponding classification level, “Top Secret,” did not come into existence until the signing of E.O. 10104 by President Harry S. Truman in 1950).
In 1954, Congress amended the Atomic Energy Act, establishing a new category of classified information relating to the military utilization of nuclear weapons, designated as “Formerly Restricted Data” (FRD).
The update to the original legislation was motivated by the need to share aspects of nuclear development and regulation with the civilian nuclear industry and plans for the potential use of atomic weapons with close military allies.
The 1954 revision would establish the framework for the current three levels of classification used for nuclear secrets, which are:
- Restricted Data (R.D.): Information concerning the design, manufacture, or use of atomic weapons; the production of “Special Nuclear Material;” or the use of “Special Nuclear Material” in the production of energy.
- Formerly Restricted Data (FRD): Classified information that has been removed from the Restricted Data category after it has been determined that it primarily relates to the military utilization of atomic weapons.
- National Security Information (NSI): Classified information related to nuclear energy technologies that don’t inherently fall under the R.D. or FRD classification categories.
Perhaps confusing, the classification categories for nuclear secrets only refer to the type of information it concerns.
Information in each classification category will also carry one of the three standard security levels based on the degree of national security damage that could be reasonably expected if improperly disclosed. So all R.D., FRD or NSI information will also hold a TOP SECRET, SECRET, or CONFIDENTIAL security level.
Unlike all other types of classified information, nuclear secrets carry greater applicability because they fall under legislative statutes instead of a presidential executive order.
Simply put, the predominant U.S. classification system can be changed or altered at the whim of the president and by issuing a new executive order. Nuclear secrecy, however, is the law of the land, and any changes would, very literally, require an act of Congress.
Today, these classified materials, and all nuclear power and weapons information, fall under the Department of Energy (DOE), established in 1977 following the aftermath of the 1973 oil crisis.
What Kind of Information Can Be Classified?
According to the current presidential classification directive, E.O. 13526, for information to be considered for classification, it must fall into one of the following categories:
- Military plans, weapons systems, or operations.
- Foreign government information.
- Intelligence activities (including covert action), intelligence sources or methods, or cryptology.
- Foreign relations or foreign activities of the United States, including confidential sources.
- Scientific, technological, or economic matters relating to national security.
- United States Government programs for safeguarding nuclear materials or facilities.
- Vulnerabilities or capabilities of systems, installations, infrastructures, projects, plans, or protection services relating to national security.
- The development, production, or use of weapons of mass destruction.
Information related to advanced military technology or “sources and methods” is the type of detail most people typically accept as intrinsically classified.
Yet, on the opposite end of that spectrum, data related to known deficiencies in military technology or national defense tend to be some of the more closely guarded secrets.
An example of this involves a rather unique topic that has generated some renewed interest in the past few years.
In The Debrief’s past reporting on the government’s surprising interest in “unidentified aerial phenomena,” or more commonly UFOs, many have asked how the government could withhold and classify information that some believe relates to a potential significant scientific discovery.
And while this may be true, if you have mysterious, unknown objects flying with impunity around U.S. defense installations and during military maneuvers, this would likewise represent vulnerabilities to U.S. national defense capabilities. Therefore, the answer to why many UFO reports would remain highly classified falls under category 7.
Information can be classified in two primary ways: Original Classification and Derivative Classification.
Original Classification is the formal process for determining that information meets the criteria to be classified and requires protection in the interest of national security. The authority to initiate the original classification of information falls to a limited number of senior government officials who are granted “Original Classification Authority” (OCA).
The President and Vice President, executive cabinet officials, and the Secretaries of the military departments, all have inherent original classification authority.
Aside from this, OCA is also granted to senior government officials with a “demonstrable and continuing need to exercise OCA during the normal course of operations” and possess “adequate information and expertise to make the classification decisions.”
The OCA must establish the security classification guide, outlining the classification level, reason for classification, when the information can be declassified, and any dissemination controls.
The vast majority of classified documents are created by derivative classification, or the process of “extracting, paraphrasing, restating, or generating in another form” information that is already classified to develop new material.
With derivative classification, an item’s overall classification level is established by the highest classification of information it contains.
For example, if a single paragraph from a TOP SECRET document is used to create a new document containing 500 pages of UNCLASSIFIED information, the entire document, as a whole, will be classified as TOP SECRET.
Because of this, many classified documents can contain very little classified information. This is a source of contention for government transparency advocates and claims of “overclassification.”
What About “Above Top Secret?”
Contrary to what you may have heard on T.V. and in movies, there is no security classification “above top secret.”
This doesn’t mean that highly classified information isn’t tightly controlled and that just because someone has a TOP SECRET clearance, they have carte blanche access to all TOP SECRET information.
Quite the opposite, the U.S. government maintains a robust role-based access control system called Special Access Programs (SAP).
Often misunderstood, SAPs are a formal policy that allows the government to restrict and safeguard highly-sensitive classified information to only the minimum number of people with a demonstrated “need to know.”
Within the Department of Defense, SAPs will fall into one of three categories:
- Acquisition SAPs
- Intelligence SAPs
- Operations and Support SAPs
Acquisition SAPs or programs involving research, development, testing, modification, evaluation, or procurement of new technologies make up 75-80% of all SAPs.
A SAP will also fall under three protection levels: Acknowledged, Unacknowledged, and Waived-Unacknowledged.
- Acknowledged SAPs: The majority of the inner details of an acknowledged SAP are shrouded in secrecy. However, as the name implies, the government, at minimum, admits the program exists.
Oversight for acknowledged SAPs is provided by members of Congress from the appropriate committee that a SAP falls under.
Acknowledged SAPs will also appear in budget documents, albeit by an unclassified codeword. For example, in the proposed F.Y. 2023 defense budget, one can find funding requests for items like PILOT FISH, RETRACT LARCH, CHALK EAGLE, or LINK PLUMERIA. These are the code names for acknowledged DoD acquisition SAPs.
- Unacknowledged SAPs: As the name implies, unacknowledged SAPs or “USAPs” are classified programs for which the mere existence can be denied to anyone who is not “read-in” to the program.
Like acknowledged SAPs, lawmakers from appropriate Congressional committees are still briefed and provide oversight for USAPs.
- Waived- Unacknowledged SAPs: The most closely guarded of all secrets can be maintained within waived-unacknowledged SAPs, or “Waived-USAPs.”
A Waived-USAP is an unacknowledged SAP that has been formally exempted from the majority of oversight and reporting requirements by either the Secretary of Defense or the President.
The only legislative branch members who are required to be informed of waived-USAPs are the so-called “Gang of Eight,” or the chairpersons and ranking committee members of the Senate and House Appropriations and Armed Services Committees.
Personnel who have approved access to a specific SAP are maintained in a directory called a “BIGOT” list. And while it may seem odd to refer to someone with access to highly guarded secrets as a “bigot,” the term has some unique roots going back to World War II.
The secret codeword for the 1942 Allied invasion of North Africa was “To Gibraltar,” referenced by the acronym “TO GIB.” The majority of the invasion force traveled by sea. However, certain military personnel was considered so vital to the mission that they were flown to Africa to avoid the threat posed by German U-boats. These high-value military personnel were classified using a backronym of the “TO GIB” codeword, reversing the phrase to “BIGOT.” The term stuck throughout the war, and today it is still used to describe individuals granted exclusive security access.
The legal framework for compartmentalizing and securing highly-classified information is contained within executive directives governing special access programs. However, the term SAP is primarily used for programs and operations within the DoD.
Highly classified and access-controlled information concerning or derived from one of the eighteen agencies that fall under the Office of the Director of National Intelligence, known colloquially as the U.S. Intelligence Community, is considered “Sensitive Compartmented Information” or SCI.
There are subtle nuances between the two systems. However, SAPs and SCI are essentially synonymous with access control systems designed to restrict sensitive information to only those with an authorized “need to know.”


Controlling Classified Information
The information and activities within a SAP or SCI activity are typically divided into various control systems and compartments and often further divided into sub-control systems and subcompartments.
The term “Control System” describes an umbrella security protocol for a specific subject.
The five known control systems for classified SCI information are:
- Special Intelligence (S.I.): The control system for communications intelligence and communications intercepts.
- TALENT KEYHOLE (T.K.): Intelligence gained through space-based imagery (IMINT), signals (SIGINT), and measurement and signature (MASINT) intelligence.
- KLONDIKE (KDK): The control system for geospatial intelligence.
- HUMINT Control System (HCS): Intelligence gained through or involving human sources.
- RESERVE (RSV): The control system used by the National Reconnaissance Office.
These are just the known active control systems. The Office of the Director for National Intelligence (ODNI) admits that more control systems remain unnamed “due to their sensitivity and restrictive access controls.”
In addition to these overall control systems, many sub-control systems can further restrict sensitive information.
For example, communications intelligence falling under the Special Intelligence (S.I.) control system can also have an additional sub-control system such as “Exceptionally Controlled Information” (ECI), which denotes highly-sensitive communications intelligence.
Sensitive compartmentalized information usually contains one or more “compartments,” representing a specific genus within an overall control system.
For example, within the HUMINT Control System, there are two known compartments: HSC-O, which stands for human intelligence operation, and HSC-P, meaning human intelligence product.
To try and make sense of this, consider the hypothetical scenario that the National Geospatial-Intelligence Agency set up a TOP SECRET program investigating rubidium drones being operated by an unknown foreign power under the SAP codename: HOTGAS.
In this example, only persons holding a TOP SECRET clearance, approved access to KLONDIKE controlled SCI, and read into the HOTGAS SAP, would have authorized access to the program or its classified materials.
In addition, to control systems and compartments, classified materials will also have specific dissemination controls attached to them.
In a nutshell, dissemination controls identify the extent or limitations that a particular classified document can be distributed.
Some known dissemination controls and their markings are:
- Originator Controlled (ORCON): Only the office that originated and maintains the information may approve dissemination.
- CONTROLLED IMAGERY (IMCON): Dissemination could compromise sources and analytics methods associated with geospatial intelligence.
- Not Releasable To Foreign Nationals (NOFORN): Classified information that is explicitly prohibited from being released to foreign governments, foreign nationals, or any non-U.S. citizens.
- Proprietary Information Involved (PROPIN): Indicates that classified documents contain commercial proprietary information that must be protected as a proprietary trade secret.
- Authorized For Release To (REL TO): An explicit foreign release marking that identifies classified information that an originator has predetermined to be released through foreign disclosure channels.
- USA/ [Country Trigraphs] EYES ONLY: Materials can only be disseminated to foreign nationals listed in the country trigraph.
- Foreign Intelligence Surveillance Act (FISA): Classified material contains FISA-related materials.
- Sources and Methods (SAMI): Dissemination could compromise sources and analytics methods associated with geospatial intelligence.
Classified information without additional control systems or compartmentations is called “Collateral” information. Anyone with the appropriate security clearance can access collateral information without being “read-in” to any additional control systems or compartments.
Continuing down the labyrinth of government secrecy, Special Access Programs, will also contain the control system “Special Access Required” (SAR), accompanied by a codename assigned to the program.
Of course, it should be no surprise that codenames are assigned according to a rigid formal process.
What’s In a Codename?
Within the Department of Defense, codenames are born through a process known as the Nickname and Exercise Term System, or “NICKA.”
For the Pentagon, NICKA is both a set of policies covering the selection of defense cryptonyms and a military-wide computer system that assigns and archives codenames to prevent duplication.
By policy, all codenames for classified programs, operations, or exercises within the DoD must contain two words.
The first word comes from blocks of pre-approved terms assigned to each component agency. Consequently, this means that the first word of a codename also identifies what agency a classified program stems from.
The second word is then randomly chosen by a classified computer system that ensures that two-word codenames meet DoD policy and aren’t replicated.
For example, annual DoD budget documents contain funding for SAPs with the codenames RETRACT LARCH, RETRACT MAPLE, and RETRACT ELM. The repeated first word, “RETRACT,” identifies these SAPs as being run by the U.S. Navy. The second word is the random term assigned to each specific program.
Classified special access programs will be assigned an unclassified and classified codename. So the “RETRACT” monikers are merely the unclassified codenames for these acknowledged SAPs. Each SAP will also have a classified codename known only to those persons with approved access.
However, these rules only apply to the Department of Defense. Other branches of government use differing methods for creating classified codenames.
In the Department of Justice (DOJ), agents assigned to a particular operation or program often come up with its codename. Typically, these are two-word monikers that carry some ironic relationship with an operation, such as Operation Vanilla Gorilla or Cross Country.
The U.S. Intelligence Community uses another undisclosed process for assigning cryptonyms. In at least some instances, intelligence officials working on a particular program are allowed to come up with their own official codename, similar to the DOJ.
Unlike other branches, the Intelligence Community often uses a single word as a classified codeword. The CIA, in particular, is fond of combining two separate words to create a single portmanteau term, such as OXCART, EASYCHAIR, etc.
Aside from creating some rather bizarre titles, the real purpose for codenames is as a control system for special access programs.
For example, imagine the Navy had a TOP SECRET acquisition SAP to develop a new stealth drone under the codeword BLACK LIGHT. The control system would then be TOP SECRET//SPECIAL ACCESS REQUIRED (SAR)-BLACK LIGHT, indicating only persons with a TOP SECRET clearance and approved access to the BLACK LIGHT SAP could access those classified materials.
But Remember, Nuclear Secrets Are Special
If you recall, secrecy related to nuclear energy and nuclear weapons is a beast of different nature.
Access to sensitive nuclear secrets involves an even deeper level of compartmentalization, and to gain access to this type of information, one must possess an entirely separate class of security clearances. Either a Q clearance or an L clearance.
The Department of Energy describes a Q clearance as equivalent to a Department of Defense Top Secret clearance, while an L clearance is akin to a Secret clearance. Succinctly this is correct. However, there is a little more nuance to it.
A person can work with the DoE and have only a Top Secret, Secret, or Confidential clearance and still have access to information categorized as Formerly Restricted Data (FRD) or National Security Information (NSI).
However, access to information categorized as “Restricted Data” (R.D.) or Special Nuclear Material (SNM) requires a Q or L clearance.
The authorized access by category for Q and L clearances are:
- L Clearance: Confidential Restricted Data (CRD) and Category II and III Special Nuclear Material (SNM CAT II&III).
- Q Clearance: Top Secret or Secret Restricted Data (TSRD or SRD), or Category I through III Special Nuclear Material
Like its larger classification sibling, classified nuclear secrets will also have control systems, special access requirements, compartments, and dissemination controls.
For example, much of the information categorized as Top Secret and Secret Restricted Data will also carry the “Critical Nuclear Weapon Design Information” control system, or “CNWDI” (pronounced Sin-widee).
Q and L clearances are typically only issued to non-military personnel since approved DoD clearances will allow access to information contained within Formerly Restricted Data and National Security Information, including plans covering the military use of nuclear weapons.
Nuclear secrets are almost exclusively classified through derivative classification and are often referred to as “born secrets.”
In the unofficial ranking of classification, SECRET and TOP SECRET Restricted Data are the most highly protected, enduring, and exclusive secrets safeguarded by the U.S. government.
Illustrating this point, roughly 1.6 million Americans hold active Confidential or Secret clearances. Nearly 1.2 million also have Top Secret access. Meanwhile, as of 2021, only 92,177 persons hold active Q clearances.
To put this into perspective, only 0.00003% of the total U.S. population possesses the requisite clearance to access nuclear secrets.
By federal statute, persons holding Q clearances are considered to have “Special-Sensitive Positions,” meaning they have access to information that could cause “inestimable damage” to national security if improperly disclosed.
Alternative Compensatory Control Measures (ACCM)
Within the Department of Defense, a classified gray area exists between standard security controls and special access program (SAP) protections, called Alternative Compensatory Control Measures (ACCM).
According to policy, any DoD component with original classification authority (OCA) can employ ACCM if they determine that standard security measures are insufficient to enforce need-to-know access for classified information, yet SCI or SAP protections are not warranted.
Though technically not a SAP, ACCM programs use many of the same security measures as special access programs, including the requirement to have an unclassified nickname and a “BIGOT” list of approved personnel.
ACCM is primarily used for intelligence and military special operations activities and is prohibited from being applied to acquisition programs.
In essence, ACCM allows for cutting through a lot of the cumbersome red tape associated with the formal SAP process to keep up with the often dynamic and fluid world of intelligence collection, analysis, and special operations.
Of course, perhaps unsurprisingly, there are some concerns about this realm of secrecy limbo.
A 2015 report by the DoD Inspector General’s Office found that the DoD’s ACCM programs “lacked effective oversight,” lacked detailed guidance, and were not providing yearly ACCM reports to Congress.
The DoD never formally responded to the I.G. Office’s findings, and over half a decade later, there’s no evidence of the DoD making any changes to the ACCM process to address the issues.
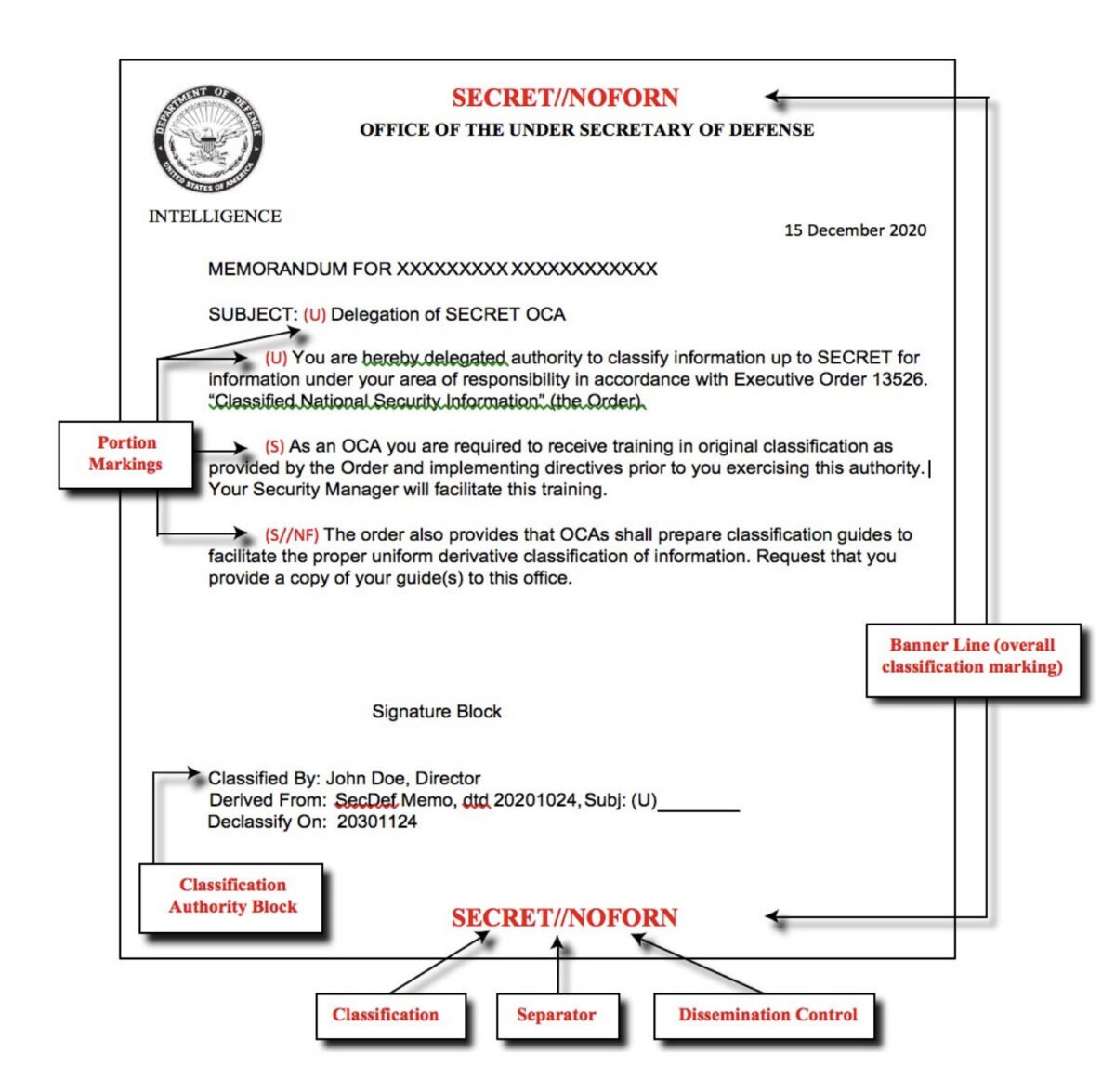

The Anatomy of a Classified Document
Thanks to the government’s strict system for marking classified documents, it is virtually impossible to pick up a classified document and not know that it contains sensitive controlled information.
Before ever getting to the inner chamber of secrets, all classified documents have color-coded cover sheets, clearly identifying the level of security classification, a warning covering the requirement to protect classified information, and in some cases, the compartment or control system associated with the materials.
The typical color codes associated with different security classification levels:
- Yellow: Top Secret/ SCI
- Orange: Top Secret or Secret/SCI
- Red: Secret
- Blue: Confidential
- Purple: Controlled Unclassified Information
- Green: Unclassified
Beyond this initial cover sheet, three essential markings will appear on every classified document.
They are:
- Classification Line or Banner Line
- Portion Marking(s)
- Classification Block
The classification line, frequently referred to as the banner line, is displayed on the top and bottom of every classified document.
A banner line will clearly identify the classification level, control systems, dissemination controls, and any other pertinent non-Intelligence Community information associated with a document.
The purpose of the banner line is to give a concise overview of the necessary clearances and access requirements for any classified document, which is achieved by following a rigid format using approved acronyms called “control markings.”
The format and hierarchy for the control markings in a banner line are:
Classification // Control System // Dissemination Controls // Non-IC Info
When applicable, Special Access Program and/or foreign government information markings will follow behind the control system and before the dissemination control markings.
Recall the earlier example of a National Geospatial Intelligence Agency (NGA) SAP codenamed HOTGAS. The banner line for all classified documents produced by this fictional program would appear as:
TOP SECRET // KDK // SAR-HOTGAS // ORCON / RSEN
To the uninitiated, this all seems like a bunch of gibberish. However, to those versed in government secrecy, this single line conveys that the document is TOP SECRET; part of the KLONDIKE SCI control system designed to protect sensitive Geospatial Intelligence; is part of the HOTGAS special access program; contains Risk Sensitive information (RSEN) related to sensitive imaging capabilities and exploitation techniques, and only the original classification authority can approve dissemination (ORCON).
The classification level is the only portion of the banner line that will always be written out in full and not displayed by an acronym.
Access to various control systems and compartments is informally referred to as “tickets.” So someone with a TOP SECRET clearance and approved access to KLONDIKE and Risk Sensitive Information would be said to “have all their tickets” to be read-into the HOTGAS program. Provided, of course, they had a justifiable “need to know.”
As also mentioned, you can easily have a classified document containing information of varying classification levels or even very little classified information altogether.
This is where portion markings come into play.
Every portion of a classified document will begin with an acronym or series of acronyms inside a set of parenthesis that describes the classification level and control systems contained in that particular segment.
For example, if the first paragraph of our fictional HOTGAS classified document did not contain any classified information, the portion marking for unclassified, “(U),” would go before the first word of the paragraph.
If the second paragraph contained TOP SECRET information related to geospatial intelligence and the HOTGAS program, the initial portion marking would be: (TS//KDK//SAR-HG).
This same format will continue throughout the entire classified document, ensuring the proper security markings are included before every specific portion.
Every classified document’s last essential detail is the “classification block.
The classification block is a separate section, typically appearing on the bottom left side of all classified documents, that clearly identifies who is the original classification authority (including name and position, or personal identifier), the reason for classification, and the declassification instructions.
The reason for classification will always cite the presidential executive order justifying the protection of sensitive information. For example, all documents created after June 2010 will cite section 1.4 of Executive Order 13526, followed by one of the eight categories that constitute material eligible for classification.
As for the declassification instructions, most classified documents will contain a date (formatted year, month, day) precisely 25 years from when the document was created. The reason for this will be explained shortly.
Example of Classification Block Format
Classified By: John Doe, Senior Program Analyst
Reason: 1.4(g)
Declassify On: 204709099
Derivatively classified documents will have a slight variation in this format. Instead of a reason, a derivatively classified document will note where it is derived from, whether it be a single document, classification guide, or multiple sources.
Some classified documents, typically those created circa 2002-2008, will also include the declassification date in the banner line. However, this format is relatively uncommon.
By policy, anything containing classified information must include all appropriate classification markings, including emails, briefing slides, electronic text messages, and handwritten working notes.
The pomp and pageantry associated with safeguarding national secrets are far more complex than most people likely realize. However, this ceremonial splendor is meaningless if you don’t have an equally robust system for physically protecting classified information.
The Real “Black Vault” of Secrecy
The art of government secrecy begins and ends with the ability to ensure the physical security of sensitive information.
As such, there is a plethora of strict policies and legal requirements governing the storage of classified information. Many measures are themselves highly-classified. However, various government policy and procedure manuals offer a general overview of how classified information is protected.
The storage requirements for classified materials depend on the information’s security classification level.
At the lowest rung of the classification ladder, CONFIDENTIAL material can be stored in a secure room or in a container that has been pre-approved by the U.S. General Services Administration (GSA) without any supplemental security measures.
What constitutes a “secure room” is carefully outlined by federal policy, including standards for constructing floors, walls, ceilings and roofs, windows, and other openings.
Similar rigid requirements govern what is considered a “GSA-approved” storage container, including the materials used and the finish’s color. For example, a class 5 GSA-approved cabinet must be able to provide protection against “20 man-hours of surreptitious entry, 30 man-minutes of covert entry,” and “10 man-minutes of forced entry.”
SECRET information can be similarly stored in a secure room and GSA-approved container. However, wherever SECRET materials are kept there must also be one of the following supplemental controls:
- Continuous protection by guards or duty personnel.
- Inspection by guard or duty personnel every four hours.
- An intrusion detection system (IDS) with a 30-minute response time.
The requirements for storing TOP SECRET information are the same as SECRET, except that these materials must also be kept in areas that maintain “security-in-depth” and be monitored by intrusion detection systems, with a 15-minute response time.
In exceptional circumstances when TOP SECRET information cannot be surrounded by security-in-depth,” there must be a 5-minute response time by security personnel to intrusion alarms.
These minimum security requirements only apply to collateral classified materials or info that does not carry additional control systems or compartments.
Sensitive compartmented information (SCI) can only be stored, viewed, or even discussed within specially designed facilities known as a “Sensitive Compartmented Information Facility” or “SCIF.”
SCIFs can be permanent secure rooms, such as the Situation Room in the White House, or found in airplanes, onboard ships, and even in private residences of high-ranking U.S. officials. SCIFs can also be temporary facilities, like a hotel room or a special container, whenever highly-classified SCI information must be discussed by lawmakers or military officials while traveling.
Ultimately, what determines if a permanent or temporary structure is a SCIF is that it meets a set of rigorous standards, ensuring anything discussed, seen, or stored within, doesn’t leave the confines of the area. In addition to intrusion alarms or armed guards, a SCIF has a variety of technical countermeasures to prevent electronic eavesdropping, both inside and outside the facility.
Within buildings like the Pentagon, you can find joint-use SCIFs or SCIFs that are shared by multiple individuals and serve as temporary meeting rooms where SCI information can be discussed. However, most highly-classified programs have specific SCIFs that can only be used by persons approved for a particular special access program (SAP) or security compartment.
Working SCIFs have secure communications centers, with computers hooked up to secure intranets only used to access classified information. For example, the Secure Internet Protocol Router Network or SIPRNet is used by the DoD to access SECRET info, while the Joint Worldwide Intelligence Communications System (JWICS) is used for TOP SECRET and SCI materials.
Exceptionally sensitive information will often use a two-person integrity system, meaning two cleared individuals are required to access classified materials.
These same extreme measures also apply to secrets that can’t necessarily fit in a SCIF, like a prototype aircraft or other highly-classified technologies.
For example, Area-51 is already well known for its reclusiveness, with personnel being flown daily to work at the Nevada test site. Even then, if a classified platform has to be brought out into the “open,” say for a test flight, all personnel not working on or read into the program are confined in windowless, soundproof areas and under armed guard until that platform is out-of-sight.
Of course, Area-51 is just the most well-known of the U.S. government’s “Black sites.” There are other more obscure areas where highly-classified technologies are tested and developed, like San Nicholas and San Clemente Islands off the West Coast or Andros Island on the East coast.
Because of the extreme measures placed on the physical protection of classified information, whenever national secrets leak out, it’s almost entirely because someone with approved access illegally releases them.
To mitigate the risk of insider threats, a person must undergo a comprehensive background check before being issued a security clearance. Depending on the backlog and one’s history, the process for a single-scope background investigation (SSBI) to gain a TOP SECRET clearance can take upwards of 8 months to a year.
Of course, the background clearance system is far from flawless.
Before ever leaking TOP SECRET documents related to Russian hacking attempts during the 2016 presidential election, NSA contractor Reality Winner was able to pass an SSBI in light of publicly sharing pro-Taliban, pro-Iranian, pro-Russian, and anti-American propaganda on her Twitter page.
The job of preventing the loss of classified information falls on an intelligence sub-discipline: counterintelligence.
Countering Security Threats
Counterintelligence, simply put, is the act of protecting national secrets from unauthorized release or foreign espionage. However, the process of doing this can be complex and involve various differing spycraft techniques, including defensive, offensive, passive, and active operations.
Defensive counterintelligence involves identifying areas that could be exploited by foreign intelligence services, malign influence, or insider threats. This typically consists of gaining insight into an adversary’s thinking and can include “red team” exercises, where counterintelligence agents will play the role of an adversary trying to gain access to protected areas or classified information.
Offensive counterintelligence or “counterespionage” is the practice of actively trying to subvert enemy espionage or attacks against friendly intelligence services. This can involve recruiting foreign agents or any actions that could deny resources to a hostile intelligence service, such as kicking out diplomats believed to be foreign spies.
Passive counterintelligence can involve ensuring that existing security controls and procedures are followed or monitoring systems that might identify anomalous behaviors by persons holding a security clearance.
For example, if a person with access to classified information suddenly started making a string of expensive purchases, counterintelligence agents might investigate the risk that this person is selling secrets to a foreign intelligence service.
Active counterintelligence can closely mirror defensive and offensive counterintelligence in that it involves proactively trying to ensure secrecy. However, active counterintelligence involves measures devoted to broadly hiding sensitive activities instead of being aimed at a specific adversary or foreign intelligence service.
Active counterintelligence activities can involve deception, misdirection, or misinformation to conceal the true nature of classified information or activity. For example, special access programs can often have a “cover story” or a fictional description of the work being done to conceal another classified activity.
To help catch undiscovered espionage activities, an active counterintelligence trick could be to use a “dangle,” or intentionally seeding particularly attractive, but often false, information to track its movement.
Some countries have independent counterintelligence agencies, such as the United Kingdom’s MI5. In the United States, the Federal Bureau of Investigation will often take the lead on counterintelligence investigations, while individual federal agencies typically have specific departments to oversee day-to-day counterintelligence activities.
In the myriad world of secrecy, counterintelligence can be considered the “tactical” side of keeping secrets.
Declassifying Secrets
The belief that something involves sensitive information does not necessarily mean it is a legitimate national security threat. However, provided the one holding that belief has been granted original classification authority (OCA), perceived privileged information can quickly become shrouded by classification.
Simply put, past all the formality and rigid policies, fundamentally, what determines if something is classified can be largely subjective.
Moreover, what is justifiably classified today will inevitably become irrelevant at some point in the future.
For example, the long-range, high-altitude SR-71 “Blackbird” was once a closely guarded secret, flown only under cover of darkness from the hermitic confines of Area-51. Today, however, one can examine the exotic delta-wing spy plane up close and for free at the Smithsonian National Air and Space Museum’s Steven F. Udvar-Hazy Center in Chantilly, Virginia.
The complicated process of declassification involves peeling back secrecy when it has been improperly applied or more frequently when it is no longer relevant.
In 1995, President Bill Clinton signed Executive Order 12937, ordering the sweeping declassification of national defense documents held in the National Archives. Following this, Clinton also signed Executive Order 12958, which in addition to creating new standards for identifying and protecting classified information, led to the unprecedented declassification of 43.9 million formally classified documents.
These newly declassified documents were all historical, dating back to World War II and to the 1970s. However, this amounted to nearly 14% of the National Archive’s holdings of classified materials.
President Obama’s 2009 Executive Order 13526 amended previous decrees, expanding government transparency and providing the current basis for how classified information becomes declassified.
Under the current executive law of the land, agencies must automatically declassify all documents after 25 years. Hence, the previously discussed reason why the declassification date on documents will typically always be exactly 25 years from the date it was created.
There are, however, nine narrow exemptions to the automatic declassification rule.
Those exemptions include examples like revealing the identity of a confidential human source or plans involving weapons of mass destruction. Principally, an agency must prove that declassification of information developed 25 years prior is still relevant to national security.
E.O. 13536 also mandated establishing a systematic declassification review for records less than 25 years old, which may offer historical value and no longer meet the requirements to be classified.
Finally, Obama’s executive order set up the process whereby anyone, including the average citizen, can request a mandatory declassification review. If a mandatory declassification review is asked for, an agency must examine records every two years to determine if they still meet the requirements for classification.
The mandatory declassification review process has successfully led to the release of numerous formerly restricted documents, though the process is typically lengthy and can take years.
Often, the general public’s first step to uncorking privileged information begins with filing a request under the U.S. Freedom of Information Act (FOIA).
Enacted by Congress and signed into law by President Lyndon B. Johnson in 1966, FOIA allows any member of the public, including non-U.S. citizens, to request unreleased information and documents controlled by the U.S. government.
Requests for the release of information that is classified will be denied. However, FOIA provides a path for restricted information to face an administrative appeal by an agency’s legal counsel. If this fails, a requester has the right to judicial review by launching civil litigation, which can go as high as the Supreme Court.
That said, because classification authority derives from the president’s executive privilege, legitimately classified information cannot be released by the courts. Instead, the successful overturning of FOIA denials will involve one of the other nine legal exemptions covering non-classified information, including:
- Information related solely to internal agency personnel rules.
- Trade secrets or proprietary information.
- Privileged communications, such as attorney-client privilege or agency deliberative processes.
- Information that would invade someone’s personal privacy.
- Information that could interfere with law enforcement proceedings.
- Information on financial institutions.
- Geological information on wells.
- Any other non-classified information that is prohibited by federal law.
Satisfying disclosure requirements mandated by FOIA while protecting classified or exempted information often results in agencies releasing heavily redacted documents. Sometimes comically, as in the case of a FOIA request to Amtrak for complaints regarding its lounge cars.
The national rail company released one page marred with black redactions, except for the phrase, “Pax stated that again his sausage was cold & his wife had a black curlie [sic] hair in her…”


The act of declassification is a systemic process. Outside of those with original classification authority, the sole responsibility for the vast majority working around government secrets is to safeguard that information unless officially told otherwise.
Security oaths and non-disclosure agreements are indefinite. Unless formally declassified, everyone with access to classified information is expected to take those secrets to the grave.
Well… almost everyone.
Can The President Declassify Anything They Want?
The question of what power a U.S. president has over the classification system has become one of the central themes surrounding recent allegations that former President Donald Trump improperly retained highly-classified documents.
Because the entire classification system is authorized and established by presidential executive order, a sitting U.S. president technically has the authority to classify or declassify anything they want at any time.
Typically, when a president wants to declassify something, they will direct officials with primary responsibility for the information to review it with the expectation of making it public.
An excellent example of this was when President Trump ordered the declassification of files related to the assassination of President John F. Kennedy. While many new documents were released in 2018, ultimately, Trump allowed certain records to remain classified based on pressure from the CIA and FBI that the information could still negatively impact national security.
On rare occasions, a president will declassify something directly, without any input or review by the agency responsible for the record. This happened in 2004, when President George W. Bush personally declassified a portion of his presidential daily intelligence brief showing a month before the September 11 terrorist attacks, he had been warned, “Bin Laden determined to strike in U.S.”
In each of these instances, regular declassification procedures have been followed, leaving no question as to whether the information is still considered national security information.
In defense against allegations of unlawfully retaining classified information, former President Trump has claimed he declassified the information found at his Florida golf resort through irregular channels while still in the White House.
This has created an unprecedented situation, as no legal precedent or federal statute requires a sitting president to follow any established procedure for declassification.
Under the current classification system, if a president simply says something is declassified, it is no longer considered restricted national security information. Whether or not the president announces that information is now declassified is seemingly irrelevant. At least in the eyes of the law.
Ironically, Trump is the only U.S. president to have also forced a legal precedent on what constitutes proper presidential declassification.
In 2020, a federal appeals court found that “declassification, even by the president, must follow established procedures.” The ruling was in response to a lawsuit claiming Trump’s mention of a covert program in a tweet meant information related to the program should be now available through the Freedom of Information Act.
A president mentioning classified information on social media is indeed another unprecedented event. However, this prior legal ruling has little bearing on current allegations because Trump never said he had declassified the program. He simply violated security procedures by publicly mentioning it.
If the courts were to take Trump’s claims of secret declassification seriously, this would mean that not only would the information in recovered documents no longer be considered national security information, but also the underlying information contained within them would have to be declassified across the board.
Depending on the classified material, this could have a wide-ranging ripple effect on national secrets far beyond just what is contained in the documents found at Mar-a-Lago.
The Washington Post has also claimed that the FBI recovered records related to a foreign government’s nuclear weapons capabilities. Citing unnamed sources, the Post did not identify the foreign government named in the classified document.
If true, this would add another unique wrinkle to an already extraordinarily complex case. As previously discussed, information involving nuclear secrets, or “Restricted Data,” is defined by federal statute, not by presidential executive order.
The Atomic Energy Act establishes that only the Department of Energy can initiate the process of declassifying Restricted Data. The president’s only explicit role in the process is acting as a tie-breaker if the Department of Energy and Department of Defense disagree on whether something should be declassified.
Under certain circumstances, the president can also direct the DoD to share Restricted Data with allied nations, such as planning for mutual defense. However, Congress failed to give the president the authority to declassify nuclear secrets at will.
So if there were Restricted Data documents, former President Trump alone, would not have had the authority to declassify them.
Of course, this could all be a moot point. The classified documents in question may not contain Restricted Data, or the Washington Post’s tip could be wrong.
The DoJ’s focus doesn’t seem to be on Trump’s mere possession of classified materials. Instead, the search warrant affidavit highlights federal laws covering the obstruction of justice and willfully preventing the government from recovering a host of documents that also includes classified material.
Nevertheless, given the issues highlighted by recent events, it’s hard to imagine that legislative or judicial changes won’t eventually come out of this to better establish a president’s role and power over classified information.
The Unintended Consequences of Secrecy
The goal of classification tiers, special access controls, compartmentalization, or counterintelligence is to ensure the utmost protection of secrets that could pose a risk to national security. However, in some instances, compartmentalization and extreme secrecy can have unusual unintended consequences.
As was the curious case of “FOGBANK,” a codeword for a classified material used in America’s W76, W78, and W88 nuclear warheads.
In the late 1990s, the Department of Energy began a program to extend the service lives of nuclear weapons, including refurbishing the mysterious FOGBANK material in older nuclear warheads.
The plan quickly ran into problems when it was discovered that secrets surrounding FOGBANK had been so closely guarded and compartmentalized that the DoE could find only limited records of the manufacturing process. The production facility had long been decommissioned, and no one even knew who had been involved in initially creating FOGBANK.
Producing the mysterious substance, evidently, includes using toxic, highly volatile solvent acetonitrile, making the entire process of blindly reproducing FOGBANK all the more fun.
The DoE wouldn’t successfully reverse engineer FOGBANK until 2009, and only after numerous setbacks and a more than $100 million investment.
Ultimately, it’s impossible to know just how much highly-classified information has disappeared into the labyrinth of extreme secrecy. It’s unlikely that FOGBANK is an entirely isolated incident.
So who knows! Maybe there really is a crashed alien spaceship tucked away and forgotten in some nondescript government warehouse.
As unlikely as that might seem, the fact remains that the U.S. government did actually lose a vital material used in the deadliest weapons ever known to humanity.
“Secrecy is What is Known, But Not to Everyone”
In an April 1961 speech before the American Newspaper Publishers Association, President John F. Kennedy said, “The very word secrecy is repugnant in a free and open society; and we are as a people inherently and historically opposed to secret societies, to secret oaths, and to secret proceedings.”
Eloquently spoken, President Kennedy, of course, also knew that when it comes to national security, there is an unavoidable necessity for secrecy. Yet this does not mean that the former president’s words don’t also ring true.
The mere existence of secrets tends to cause internal trepidation. Particularly in free and democratic societies, when the government is the one keeping the secrets.
There is an inclination to assume that the government purposefully conceals information for public detriment. Essentially, “The government won’t tell me because they must be trying to harm me.” This belief is the cornerstone of all governmental conspiracy theories.
Distrust of government secrecy is only heightened by actual instances of individuals working in government using the classification unnecessarily, in error, or for their own malign self-interest.
Thanks to an innate distrust of surreptitiousness, incidents of misuse or abuse often become the dominating belief of government secrecy. In fairness, there is a measure of wisdom in being able to woefully say, “I knew it!” rather than exclaiming in ignorance, “Et Tu, Brute!” whenever things go wrong.
Incidents like “Stellar Wind,” the 2001-2004 warrantless surveillance program authorized by President George W. Bush, or “Enhanced interrogation techniques,” also authorized by President Bush in the wake of 9/11, tend to dominate the collective conscience and become the familiar envoy of government secrecy.
However, intrinsically, these prevailing instances of misuse speak less about government classification than how secrecy can be abused.
A more prevalent problem is “overclassification,” or the erroneous classification or the well-intended classification of information that could be better served if publicly known. This is a problem not just for public transparency but also for the government itself.
For over two years, DoD officials have been pushing for declassifying a top-secret U.S. space weapon. Military leaders have said that disclosing this secret technology will deter countries, most notably China and Russia, from using anti-satellite weapons on U.S. space systems.
Lawmakers approved for classified briefings have periodically asked for some intelligence reports to be declassified so an oblivious American public can be better informed about threats to national security.
In truth, behind the alluring veil of government secrecy is a confusing tapestry dominated by an endless stream of bureaucratic trivia, true national security secrets, such as confidential intelligence, military plans, or advanced defense technologies, and yes, occasionally, the good-old-fashioned cover-up or crime.
This last aspect, or abuse of secrecy, represents the “repugnant” secrets President Kennedy was referring to.
And when it comes to ferreting out those rare but actually concerning, “repugnant” aspects of government secrecy, the most vital step is having some knowledge and understanding of how the entire system works. This primiarly involves all those mundane parts that never make it into the James Bond films.
So after taking this deep dive into the working of government secrecy, hopefully, one will feel confident in offering a cynical gaze to anyone claiming to publicly discuss classified information and not doing so from within a federal jail cell or as Edward Snowden’s new roommate in Russia.
Or flash a skeptical frown at anyone declaring on Reddit that they have, or once had, a security clearance higher than the president upon remembering the entire classification system flows from the president’s power and authority.
Perhaps, now armed with just some passing knowledge of all meticulous security measures taken with classified information, one might even raise a suspicious eyebrow at anyone claiming to have just “accidentally” stumbled upon some highly-classified technology or material.
At a minimum, when it comes to the many varied and complex inner workings of government secrecy and classified information, one can at least say, “Now, I know.”
And as G.I. Joe famously said, “Knowing is half the battle.”
Tim McMillan is a retired law enforcement executive, investigative reporter and co-founder of The Debrief. His writing typically focuses on defense, national security, and the Intelligence Community. You can follow Tim on Twitter: @LtTimMcMillan. Tim can be reached by email: tim@thedebrief.org or through encrypted email: LtTimMcMillan@protonmail.com

