A mysterious person or group is currently waging cyberwar on online forums used by Russian hackers and cybercriminals on the dark web.
According to security analysts, at least four major Russian-language cybercrime forums, serving thousands of experienced cybercriminals, have been hacked in the last few weeks. In at least two instances, hackers made off with users’ email and IP addresses and hashed passwords.
The hacked forums serve as organized criminal marketplaces and hubs for a host of cybercrimes including, malware distribution, money laundering, identity and credit card theft. With these recent breaches, many forum users are now understandably concerned these mysterious hackers could reveal their real-life identities.
Who’s behind this rash of cyberattacks is unknown. However, whoever it is, they possess the sophistication and technical expertise to exploit some of the longest-running and most revered online forums used by Russian cybercriminals.
Some have speculated the rash of attacks is the work of rival hacker gangs. However, others have theorized that based on the level of sophistication, the hacks may result from a state-sponsored intelligence or law enforcement agency.
Citing unnamed sources, The New York Times recently reported the U.S. Government was planning to launch a series of “clandestine” cyberattacks on Russia to retaliate against the SolarWinds hack. Considering the ongoing attacks on Russian cybercrime forums, one can’t help but wonder if maybe the U.S. isn’t “planning” but currently engaging in retaliation by targeting Russian hackers rather than the Kremlin directly.
“Only intelligence services or people who know where the servers are located can pull off things like that,” KrebsOnSecurity quoted one Russian hacker and dark web user.


According to Krebs, the first hacks began in January 2021, when administrators of the longtime Russian cybercrime forum Verified revealed someone had hacked the site’s domain registration. Administrators said the hackers had redirected the site’s domain to another internet server they controlled.
“It should be clear by now that the forum administration did not do an acceptable job with the security of this whole thing,” read a message to Verified forum users by the purported hackers. “Most likely just out of laziness or incompetence, they gave up the whole thing. But the main surprise for us was that they saved all the user data, including cookies, referrers, IP addresses of the first registrations, login analytics, and everything else.”
Security firm Intel 471 says the unknown hackers made off Verified’s entire database, including all registered users’ information and private messages, hashed passwords, posts, threads, and $150,000 worth of cryptocurrency.
In February, another popular Russian cybercrime forum, Crdclub, announced unknown actors had successfully compromised the administrator’s account. By seizing control of Crdclub’s administrator account, the mysterious hacker then lured forum customers into using a money transfer service that resulted in an unspecified amount of money being diverted into the hacker’s pocket.
A few weeks later, on March 1, the next-largest and most popular Russian cybercrime forum after Verified, Exploit, announced it had been compromised.
Intel 471 reports, Exploit administrators said they detected an unauthorized secure shell (SSH) access to a proxy server used for the protection from distributed denial-of-service (DDoS) attacks, in addition to an attempt to dump network traffic. The extent of the Exploit hack hasn’t been fully revealed.
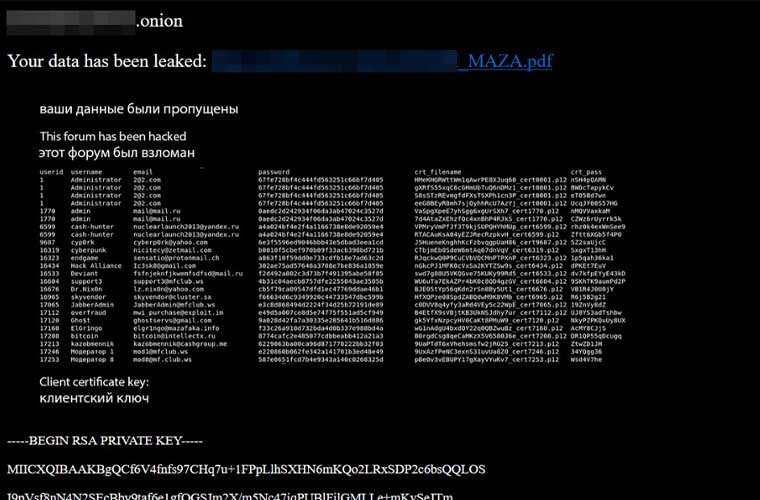
Two days later, on March 3rd, users to the invite-only forum used by the most experienced and infamous Russian cybercriminals, Mazafaka (a.k.a “Maza,” “MFclub), were redirected upon signing in to a page saying, “Your data has been leaked. This forum has been hacked.”
Included with the warning was a PDF file containing 3,000 rows of user data, containing usernames, partially obfuscated password hashes, email addresses, and other contact details. Intel 471 reports the leaked data correlates with previous research, confirming Maza’s databases have indeed been breached.
Hackers also leaked the private encryption key allegedly used by Maza administrators and the ICQ numbers for many of the forum’s users. Krebs notes that user ICQ numbers leak is notable because it can allow security researchers to connect multiple accounts to the same user across differing criminal forms, who use differing nicknames over time.
With four high-level Russian cybercrime forums, all hacked within weeks of each other, many Russian hackers are scrambling, wondering what is exactly going on.

Reportedly, many Russian cybercriminals fear the recent rash of hacks could be a new tactic aimed at trying to shut down Russian cybercriminal networks. “Three forums in one month is just weird. I don’t think those were regular hackers. Someone is purposefully ruining forums,” said one user of Exploit.
Given the very public nature of the hacks, Intel 471 analysts say they think it is unlikely the recent hacks are the work of law enforcement or intelligence operation.
Security firm Flashpoint also notes this isn’t the first time Russian cybercrime forums, including Maza, have been hacked. In 2011, Maza and another form, DirectConnection, were compromised with data on more than 2,000 Russian cybercriminal users and forum correspondences seized.
Yet, Flashpoint notes analysis of the Russian sentences in the redirect warning to Maza users appears to have been translated using an online translator. An automated translator could be a misdirection technique meant to confuse cybercriminal forum users, or it could indicate a non-Russian speaking actor is targeting Russian hackers.
Considering the latter possibility, one can’t help considering recent reports that the U.S. Government was planning “a series of clandestine actions across Russian networks” to signal that Russia’s SolarWinds hacking campaign had crossed a line.
Many cyber and national security experts contend that launching any significant punitive action against the Kremlin for SolarWinds would be inappropriate and counterproductive.
There’s no evidence that Russia’s hacking in SolarWinds went beyond the same type of covert intelligence gathering that the United States regularly performs, cofounder of security firm CrowdStrike and executive chair of Silverado Policy Accelerator, Dmitri Alperovitch, recently explained in an interview with Wired.
In contrast to past operations run by Russia’s GRU, such as the hacking of the Democratic National Committee and Clinton Campaign in 2016 or disruption of the 2018 Winter Olympics, the SolarWinds hack was far from reckless, going as far as including a kill switch to remove the malware from unintended targets.
Ultimately, the SolarWinds hack was an act of cyber-espionage, not categorically a cyberattack. The case is very similar to in 2015 when the Chinese government stole millions of background investigation forms in a breach of the Office of Personnel Management (OPM).
In testimony before Congress, then-Director of National Intelligence James Clapper testified the OPM hack was one of the largest cyber-crimes ever perpetrated against the U.S. Government. However, “But one thing it wasn’t? A cyberattack. At least in the true sense of the term,” said Clapper.
Essentially, security analysts assert attempts to gain intelligence on foreign governments and potential adversaries covertly is something all nations engage in, with the United States having one of the largest spy ecosystems in the world. However, espionage, by itself, is not categorically an attack.
Instead of “retaliation,” cybersecurity-focused Hoover Fellow at Stanford University, Jacqueline Schneider suggests the best response to SolarWinds would be targeting Russian hackers’ ability to carry out operations rather than the Kremlin directly. “You make their job harder to do, which makes them invest more resources, which diverts resources from other nefarious things, Schneider told Wired.
Another unnamed U.S. Government cybersecurity official recommended a similar “brushback” approach in response aimed at Russian hackers. “That brushback tactic may not actually differ from a ‘retaliation’ strike in substance. But framing it as a direct warning or counter strike to adversary hackers themselves rather than a norm setting ‘punishment’ for their bosses in the Kremlin could make that action more effective,” the official told Wired.
If the United States has unleashed its own advanced persistent threat teams, such as the National Security Agency’s (NSA) uber-secret and shadowy “Equation Group,” this might resemble precisely the type of “hacking the hackers” approach security analysts recommend.
Musing the underlying purpose for the recent cyber attacks, “Perhaps they work according to the following logic,” said one Russian user of Exploit. “There will be no forums, there will be no trust between everyone, less cooperation, more difficult to find partners – fewer attacks.”
Intel 471 says, “Whomever is behind the actions has indirectly given researchers an advantage. Any information unearthed from the breaches aids in the fight against these criminals due to the added visibility it gives security teams who are tracking actors that populate these forums.”
Don’t forget to follow us on Twitter or Facebook to weigh in and share your thoughts. You can also get all the latest news and exciting feature content from The Debrief on Flipboard, Instagram, and don’t forget to subscribe to The Debrief YouTube Channel to check out The Official Debrief Podcast.

